Spear phishing: how hackers use personal information to target users
- HacWare
- Aug 14, 2023
- 5 min read
What is spear phishing?
Spear phishing is a type of phishing message that’s highly targeted and personalized and is usually harder to detect than mass-phishing campaigns.
To create these personalized campaigns, hackers piece together data they can find or buy online to build a profile of an individual or group of users (like an accounting team or a group of people who frequent a certain business or event). They can then better target that profile with a spear phishing campaign.
How to spot a spear phishing attack
Spear phishing attacks are built to be hard to spot, and they’re effective! Two-thirds of all breaches resulted from spear phishing attacks in 2022, despite accounting for only .1% of email-based attacks that year.
Here’s what you can look out for in your inbox:
Over-personalized messages. If an email includes more of your personal information than you would expect, or than you were aware of sharing, this could be a red flag.
Under-personalized messages could also be a sign of spear phishing. A hacker may ask a user to fill a gap in their data by including incorrect information or asking users to confirm or deny their details.
Unusual requests. Despite personalization that may make an email appear legitimate, be aware of the types of requests you typically receive, and be cautious of anything that falls outside that norm.
Send times outside the norm. Pay attention to when you normally receive emails from certain individuals and be cautious if you receive something outside normal time frames or business hours.
Inconsistent information, links or other details. Hover over every link in every email before you click and if you find even one link that doesn’t go to the expected address, it could be a phish.
In the example of a spear phishing attack below, you can see signs like over-personalization and what is likely an unusual request for the recipient to read a claim and respond quickly. There are also signs of a typical phishing message in the example, such as the sense of urgency mentioned and the shortened, potentially malicious link.
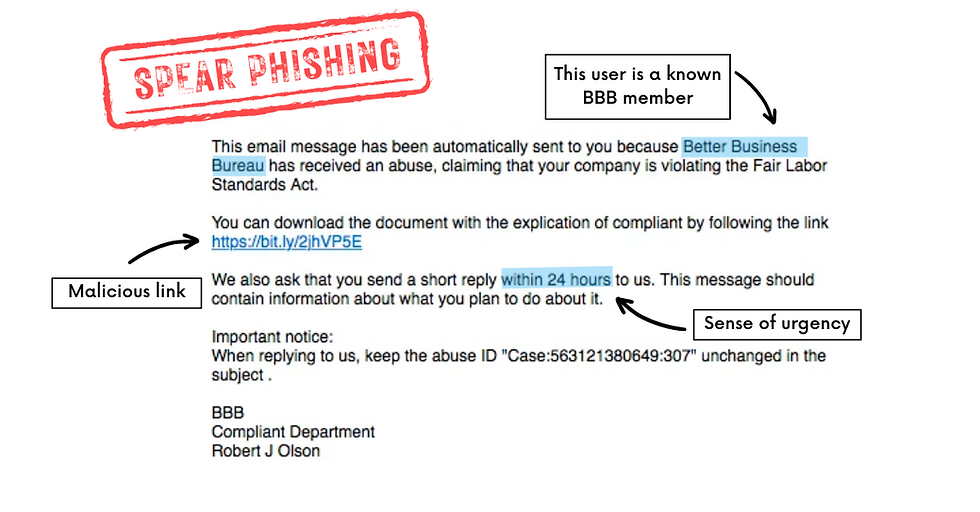
The key factor in the spear phishing example above is the bad actor’s knowledge of the potential victim’s involvement with the Better Business Bureau. By using this information, the attack is more targeted, appears more legitimate and may be more likely to induce a click from the recipient.
How hackers find & target their spear phishing victims
Before a spear phishing message is sent, the bad actor has likely done some work pulling together victim profile information or purchasing pre-built profiles. They look for groups of users with something in common (like being a member of the Better Business Bureau in the example above), so they can send attacks to multiple people while still personalizing the message content with details that are relevant to everyone in the group.
Any data that’s available online, including information that’s commonly public, like your name or general location, could be used by a hacker to build out your profile or get you included in a targeted group. While a lot of the information hackers include in victim profiles (like your name or general location) isn’t typically considered “sensitive,” it could still reveal details that could tie one piece of information to another or help build out a more robust user profile that could be used in a targeted attack.
Why is there so much sensitive data available?
Cyber attacks and potential breaches that could include personal and sensitive information are happening all the time —one occurs every 39 seconds according to Security Magazine.
Each attack has the potential to reveal more, new or different information about individual users. A March 2023 cyberattack on the Tennessee-based Chattanooga Heart Institute revealed that an unauthorized third-party gained access to their network and obtained copies of patient data, including: names, mailing addresses, social security numbers, health insurance information, lab results, medications and demographic and financial information.
While the Chattanooga Heart Institute notified the affected individuals and is providing credit monitoring services to the victims, that private information is now potentially available to bad actors.
How can you protect your sensitive data to avoid spear phishing attacks?
First, it’s important to understand what’s considered sensitive data. While there’s no exact definition of what's considered “sensitive” data and what isn’t, data that’s typically considered “sensitive” in terms of a data breach includes: information that if exposed or accessed by an unauthorized individual, could cause harm or other negative consequences.
These five data types are generally considered sensitive information:
Personal identifiable information (PII): your driver's license number, social security number, date of birth, home address or any information that could be used to identify a specific person.
Financial information: your bank account information or credit card number.
Health information: medical records, diagnoses, or anything protected by HIPAA.
Passwords: authentication data and security questions.
Confidential or proprietary business & government information: trade secrets, intellectual property or classified government documents.
This is a wide-ranging list and it can vary based on compliance, regulations and industry standards.
To protect your sensitive data and better secure yourself against attacks like spear phishing, there are many things you can do. Here are a few easy ways you can increase your privacy and better protect yourself from attacks:
Use strong passwords and MFA: Create complex passwords that are not easily guessed, and utilize multi-factor authentication whenever possible. Learn more about MFA.
Review your social media privacy settings: Spend some time checking the privacy settings on your social media accounts. You can likely limit the amount of personal information you share publicly and update who has access to the content or information you share.
Use secure wifi networks: Instead of logging on to any available wifi network, be cautious about where you connect. Learn more about keeping your data secure on public wifi networks.
Update your devices and software regularly: Staying on top of updates keeps you secure from known vulnerabilities that are often patched or otherwise closed when you perform the update.
Be vigilant when it comes to phishing: Avoid clicking on unknown attachments or suspicious links and verify a sender’s identity through a secondary channel before responding to unsolicited messages or requests for personal information.
It may also be helpful to check your email address and phone number on a site that scans for information revealed in data breaches like Have I Been Pwned?. There you can see if your personal information is already available to hackers to give you another reason to stay vigilant.
No matter how your personal and or private information is revealed, once it’s out there hackers could potentially use it to target you in a spear phishing or other social engineering attack. Keep this in mind before clicking on or replying to messages in your inbox — you never know what a hacker has discovered or how they might use it in an attempt to get you to click!
Learn more about HacWare: MSP partners can decrease the likelihood their end users will click on a phishing email by 60%. Let us educate your end users with automated, AI-driven phishing simulations and under three-minute micro-trainings to keep user attention and improve learning outcomes.
Learn more about our partner program and how we can support your MSP's growth!
